How to Prevent DDoS Attacks? – Best Practices to Follow

During a DDoS attack, a hacker floods a server or network with bogus traffic. Too much traffic overloads the system and disrupts connectivity, preventing genuine user requests from being processed. During downtime, revenue is lost, and customers are dissatisfied.
Business owners can know how to prevent DDoS attacks by staying ahead of hackers with this article. Here are some practices to help prevent a DDoS attack and recover quickly from one.
What Is a DDoS Attack?
By flooding a network, service, or server with fake traffic, DDoS attacks aim to crash a computer or network. As a result, the system becomes overwhelmed, causing the system to slow down or crash as a result of the spike in messages, connection requests, or packets.
In DDoS attacks are used primarily to: In addition to blackmailing businesses with ransoms (similar to ransomware), they are commonly used to:
- Disrupt communications or services.
- Inflict damage to the brand.
- Utilize the downtime of your competitor’s website to gain an advantage.
- Interruption of incident response.
Whether a Fortune 500 company or a small e-tailer, how to prevent a denial of service attack can lead to serious consequences. These are some of the most common DDoS targets:
- Retailers on the Internet.
- Providers of IT services.
- Fintech and financial companies.
- Entities under government.
- Gambling and gaming companies online.
Botnets are typically used by attackers to cause a DDoS attack. It is a computer, mobile device, or IoT gadget network controlled by an attacker that has been infected with malware. Using these “zombie” devices, hackers send huge numbers of requests to the IP address of a target website.
If enough requests are sent by the botnet, the online services (email, websites, web apps, etc.) will slow down or fail. A Radware report states that an average DDoS attack lasts for the following amount of time:
- An hour’s worth of services are unavailable for 33%.
- The majority of them last less than a full day.
- About 15 percent of them last for a month.
In general, DDoS attacks do not directly result in data breaches or leaks; however, the victim will have to spend time and money restoring service. When DDoS attacks are not prevented, business is lost, shopping carts are abandoned, customers become frustrated, and reputation is harmed.
DDoS attacks are often used to distract attention from other, more damaging threats. Discover cyber security attack types that are the most dangerous to your business and stop a DDoS attack.
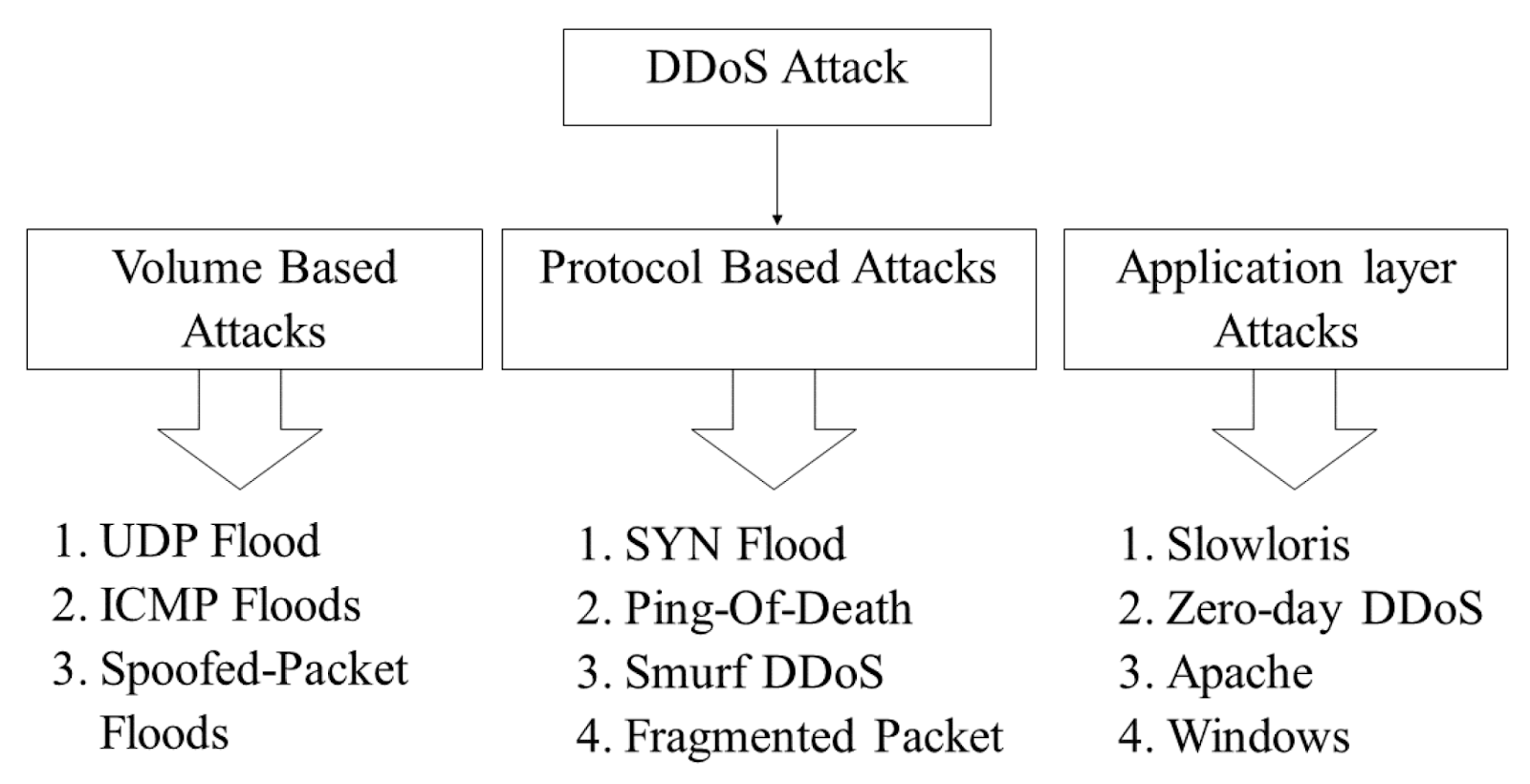
Types of DDoS Attacks
Hackers use a variety of strategies to cause a distributed denial of service, even though all preventing ddos attacks are aimed at overwhelming a system with too much activity.
There are three types of attacks:
- Attacks can be made against the application layer.
- An attack on the protocol.
- Attacks on volumetrics.
While each method relies on a different technique, a skilled hacker can employ all three approaches to completely overwhelm a single target.
DDoS protection is included with all Serverwala servers at no extra charge. Our lightning-fast DDoS mitigation infrastructure and automated traffic filtering will keep you online 24/7.
Application-Layer Attacks
Application-layer attacks target and disrupt specific apps instead of an entire network. Hackers bombard a target server with so many HTTP requests that it can no longer respond.
The request per second (RPS) is a measure used by security specialists to measure app-layer attacks. These attacks are typically directed at:
- Apps for the web.
- Apps that connect to the Internet.
- Cloud computing services.
When trying to prevent DDoS attacks of this type, security teams often have trouble telling legitimate HTTP requests from malicious ones. Some hackers can even orchestrate an application-layer attack with only one device, using fewer resources than other DDoS strategies.
Layer 7 attacks are also known as app-level DDoS attacks.
Protocol-based attacks
Attacks on the protocols (or network layer) exploit vulnerabilities in the protocols or procedures governing internet communications. The goal of an application-level DDoS is to slow down a specific app, but that of a protocol attack is to slow down the entire network.
DDoS attacks based on the protocol are the following:
- Syntax floods: This attack exploits the handshake procedure during TCP connections. Fake IP addresses are used to send TCP requests to the target. After responding to the sender, the target system awaits confirmation of the handshake from the sender. By not sending the response, the attacker keeps piling up incomplete processes, crashing the server eventually.
- Smurf DDoS: A hacker creates an IP packet attached to a false IP address using malware (spoofing). A ping message is included in the package that asks the network for a reply. In an infinite loop, the hacker sends the replies (echoes) back to the network IP address, causing the system to crash.
The protocol attack is measured using packets per second (PPS) or bits per second (BPS) in the field of cybersecurity. Protocol DDoS attacks are so common because they bypass poorly configured firewalls easily.
Volumetric Attacks
Volume-based DDoS attacks overload a target’s network with false data requests, consuming its bandwidth. Users attempting to access legitimate services are prevented from doing so by the attacker’s traffic.
Volumetric DDoS attacks take the following forms:
- UDP floods: This attack allows hackers to overwhelm target hosts with stateless UDP packets.
- DNS amplification (or DNS reflection): This technique redirects high volumes of DNS requests to the IP address of a target.
- ICMP flood: This technique overloads the network with ICMP false error requests.
Botnets are at the heart of all volumetric attacks. Hackers consume all bandwidth by infecting thousands of devices with malware. DDoS attacks are commonly known as volumic attacks.
Serverwala’s Bare Metal Dedicated Servers provide robust protection against DDoS. The servers come with free DDoS protection, which ensures availability even when volumetric attacks cause high traffic.
Best Practices for Preventing DDoS Attacks
DDoS attacks cannot be prevented, but preparation and proactive measures can reduce the risks and potential impact.
Create a DDoS Response Plan
Your security team should prepare an incident response plan to ensure that staff members respond quickly and effectively in the event of a DDoS attack. Among the items you should include:
- Simple, step-by-step instructions for responding to a DDoS attack.
- Business operations: how to maintain them.
- Contacts for key stakeholders and staff.
- Protocols for escalation.
- Teams have responsibilities.
- All the tools you need in one place.
- Mission-critical systems overview.
The ability to respond to unexpected events is necessary for the continuity of business. In this article, we explain disaster recovery from start to finish.
Secure your network to a high level
To protect against a DDoS attack, network security must stop the attack. It is crucial to be able to identify how to stop a DDoS attack early on so that the blast radius can be controlled, as an attack only becomes a problem if a hacker has enough time to pile up requests.
- Network barriers that scan the traffic between networks, such as firewalls and intrusion detection systems.
- Virus detection and removal software.
- The security of network endpoints (desktops, laptops, mobile devices, etc.) so that malicious activity cannot enter the network.
- Web security tools block abnormal traffic, detect known attacks, and remove web-based threats.
- A tool that looks for consistency between the source address and the origin address to prevent spoofing.
- Network segmentation with unique security protocols and controls that separate systems into subnetworks.
A high level of network infrastructure security is also required to protect against DDoS attacks. With the help of networking device security, you can prepare your hardware (routers, load balancers, DNS servers, etc.) for traffic spikes.
You can find vulnerabilities in your network before hackers do by conducting a vulnerability assessment. For a more comprehensive analysis, you can perform a penetration test.
Have Server Redundancy
Due to the distributed nature of multiple servers, hackers are unable to attack all of them at the same time. Until a targeted system is restored after a successful DDoS attack on one server, the other servers will not be affected.
To prevent network bottlenecks and single points of failure, you should host your servers at data centers in different regions. Content delivery networks are also a good option. CDNs distribute the load between several distributed servers to compensate for the overload caused by DDoS attacks.
The colocation services offered by Serverwala allow you to create the ideal hosting environment, benefit from high security, and take advantage of a variety of managed services.
Warning Signs to Watch Out For
When your security team quickly recognizes the signs of a DDoS attack, they can act quickly to mitigate the damage.
A DDoS attack is characterized by the following signs:
- Connectivity issues.
- Performance issues.
- Single pages or endpoints are in high demand.
- Crash.
- The traffic is unusual because a small number of IP addresses are involved.
- Common user profiles (such as the system model, geographic location, and web browser version) drive traffic.
DDoS attacks do not always result in high traffic. Low-volume attacks are often overlooked as random events due to their short duration. They can, however, serve as a test or diversion for other attacks. Threats that pose a greater risk (e.g. ransomware). In other words, detecting a low-volume attack is as important as detecting a massive DDoS attack.
It would be wise to organize a DDoS awareness training program for your entire staff. It means you don’t have to wait for a member of the security team to notice the warning signs.
Network traffic is continuously monitored
DDoS activity can be detected by continuous monitoring (CM) by analyzing traffic in real-time. Its benefits include:
- Detecting a DDoS attack in real-time allows you to cut it off before the attack reaches its full potential.
- By examining typical network activity and traffic patterns, the team was able to draw a clear picture of network patterns. Once you understand how day-to-day operations look, the team is more likely to identify odd behavior.
- Detecting signs of an attack outside of office hours and on weekends is possible by monitoring continuously.
If an issue arises, CM tools contact administrators or run predefined scripts for a response, depending on their settings.
Are you interested in continuous monitoring? It is an ideal place for beginners to begin exploring Nagios, one of the most popular CM tools.
Limit Network Broadcasting
DDoS attacks typically target every device on your network in order to increase their impact. The security team can counteract this tactic by limiting network broadcasting between devices.
Limiting (or possibly turning off) broadcast forwarding can be an effective way to interrupt a massive DDoS attack. It may also be a good idea to instruct your employees to disable other services in addition to echo and charge.
Also Read: What are Edge Data Centers?
Prevent DDoS attacks by leveraging the cloud
In contrast to on-premise hardware and software, cloud-based mitigation does not have the same limitations in terms of countering DDoS threats. Using cloud-based protection, even a large volumetric DDoS attack can be handled easily.
A cloud provider can help you prevent DDoS attacks. Working with a third-party vendor offers the following benefits:
- Cloud-based providers offer comprehensive cybersecurity thanks to top firewalls and threat monitoring software.
- Public clouds have greater bandwidth than private networks.
- Redundant networks, systems, and equipment are provided by data centers.
When a business decides to use cloud-based DDoS protection, it has two choices:
- Cloud DDoS mitigation on-demand: These services activate once the provider or the in-house team detects a problem. If your stopping DDOS attacks are compromised by a DDoS attack, your provider will divert all traffic to the cloud.
- This type of DDoS protection routes all traffic through a cloud scrubbing center (at a minimal cost). Mission-critical apps cannot afford downtime, so this option is the best choice.
If you possess the required know-how, you may not have to rely solely on a cloud provider for DDoS protection. With DDoS protection that is on-demand or always-on, you can plan your traffic accordingly in a hybrid or multi-cloud environment.
Conclusion
As DDoS attacks increase in number, they are also becoming more dangerous. DDoS experts predict that by 2023, there will be 15.4 million DDoS attempts per year. According to that statistic, almost all businesses will face a DDoS attack at some point, so preparing for this type of attack should be your top priority.