How to Secure Your CI/CD Pipeline

Introduction
Securing a CI/CD pipeline is critical in today’s cybersecurity landscape. CI/CD pipelines streamline the process of developing, testing, and deploying code, automating these tasks for faster releases. However, this automation also introduces new security challenges, potentially exposing sensitive code, configurations, and data if not properly secured.
This blog will guide you through the essentials of CI/CD pipeline security, starting with a breakdown of how these pipelines work and the unique vulnerabilities they present. We’ll explore common security challenges in CI/CD, such as managing secrets and mitigating dependency vulnerabilities. Additionally, the blog will outline best practices to secure your pipeline, including strategies for access control, automated security testing, and continuous monitoring. With security threats increasingly targeting software supply chains, securing CI/CD pipelines is essential to maintain safe, efficient, and compliant development practices.
CI/CD Pipeline Explained
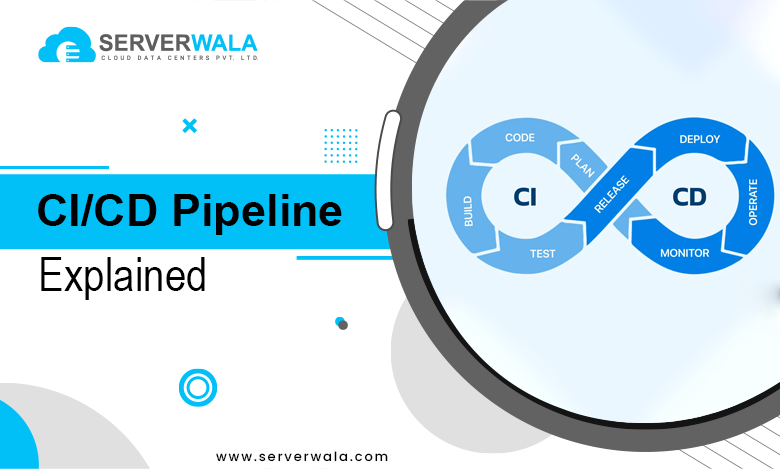
A CI/CD pipeline is a framework that automates the integration, testing, and deployment of code. This pipeline consists of two main processes: Continuous Integration (CI) & Continuous Delivery (CD).
- Continuous Integration (CI) emphasis on merging code modifications into a shared repository often. Developers can submit code modifications several times a day. Each submission triggers an automated testing process, allowing teams to recognize and sort problems early in development. This practice improves collaboration and maintains code quality by ensuring that all integrations pass automated tests.
- Continuous Delivery (CD) constructs on CI by automating the release procedure. It ensures that code is everytime in a deployable state. With CD, code changes that pass testing can be automatically pushed to a staging environment for further testing. Some entities take this a step forward with Continuous Deployment, which automates the deployment of code to production the moment it clears all tests.
How to ensure CI/CD pipeline security

While CI/CD pipeline security accelerates the software development lifecycle, it introduces unique security challenges. A compromised CI/CD pipeline can lead to the deployment of malicious code directly into production. Vulnerabilities can arise at each stage of the pipeline, making it essential to implement security measures effectively. Securing a CI/CD pipeline requires embedding security measures at every stage. Here are essential steps:
Integrate Security Scanning
Static Application Security Testing (SAST) examines source code for susceptibilities early in development, catching issues like unvalidated inputs. Dynamic Application Security Testing (DAST) assesses the application in action to recognize runtime susceptibilities, ensuring exhaustive security coverage.
Manage Secrets Carefully
Sensitive data, like API keys & passwords, should be stored in secure vaults rather than embedded in code. Role-based access controls (RBAC) help limit access to secrets, reducing potential exposure.
Limit Access Controls
Apply the principle of least privilege, rendering team members only the accessibility they require for their roles. Adding Multi-Factor Authentication (MFA) creates an additional security layer, making it tougher to gain illicit access, even if the account credentials have been exposed.
Automate Compliance Checks
Regular compliance checks can catch misconfigurations that might otherwise go unnoticed. Automating this process ensures that security standards are maintained consistently, reducing risks as the pipeline progresses to production.
Common Security Challenges in a CI/CD Pipeline

Securing a CI/CD pipeline comes with several complex challenges. Each stage of the pipeline presents unique vulnerabilities that, if left unaddressed, can expose sensitive data, introduce risks, and weaken overall security.
Exposed Secrets
Hardcoding sensitive information, like API keys and passwords, directly into scripts or configuration files is a common security lapse. If these secrets are exposed or stored without adequate protection, attackers can exploit them to gain unauthorized access to applications and infrastructure. Instead, secrets should be securely stored in vaults and accessed through proper secrets management tools, minimizing exposure risks.
Dependency Vulnerabilities
Modern CI/CD pipelines often use open-source and third-party libraries, which may contain unvetted vulnerabilities. Without rigorous monitoring, these dependencies can introduce risks that propagate through the entire application. Regular scanning of dependencies and updates are essential to prevent vulnerabilities from compromising the security of the entire build.
Insufficient Monitoring
A lack of continuous monitoring within the CI/CD pipeline can allow malicious activities to go undetected. Attackers might exploit gaps in visibility to tamper with the build, inject harmful code, or gain unauthorized access. Executing real-time monitoring and alerting systems enables detection of unusual behavior early, enabling faster response and minimizing damage.
Build Spoofing
In build spoofing attacks, unauthorized changes are made to the build environment, potentially introducing malicious code that could reach production undetected. This makes source validation and environment integrity checks essential. By verifying the source of each build and ensuring the environment’s security, teams can reduce the risk of unauthorized alterations.
CI/CD Security Pipeline Best Practices
Implementing security best practices within a CI/CD pipeline is crucial to creating a secure and resilient software delivery process. Here are key strategies to consider:
Automate Security Testing
Integrate automated security tools, like Static Application Security Testing (SAST) & Dynamic Application Security Testing (DAST), into the pipeline. These tools scan code and configurations for vulnerabilities during every CI/CD cycle, ensuring potential security problems are detected and remediated before deployment. Automating testing reduces human error and accelerates the identification of risks.
Implement Multi-Factor Authentication (MFA)
Need MFA for all users logging into the CI/CD environment. This additional layer of security prevents unauthorized access even when credentials get viral. By adding MFA to key areas, such as code repositories and build systems, organizations can significantly reduce the risk of intrusions.
Run Regular Penetration Tests
Penetration tests simulate attacks to identify weak points in the pipeline’s defenses. Conducting these tests regularly helps development teams uncover susceptibilities before malicious actors can exploit them. Pen tests allow teams to prepare and implement effective mitigation strategies, strengthening the overall security posture of the CI/CD process.
Enforce Code Signing
Use digital signatures to verify the authenticity of code before it progresses to production. Code signing ensures that only verified, trusted code is deployed, reducing the risk of introducing malicious components into live environments. This practice helps sustain the integrity of the pipeline and builds trust in the deployment procedure.
Set Up Continuous Monitoring
Execute real-time monitoring tools to recognize suspicious tasks within the CI/CD pipeline. Continuous monitoring provides visibility into pipeline operations, allowing teams to catch as well as respond to threats in real time. Alerts for anomalies, such as unusual login patterns or unexpected changes in code, enhance proactive security measures.
Adopting these practices builds a layered approach to CI/CD security. They work together to mitigate risks and protect the software development lifecycle, keeping the pipeline resilient against emerging cyber threats.
Also Read: What is Cybersecurity? Definition, Threats, Best Practices
Conclusion
Securing your CI/CD pipeline is vital to protect sensitive data and code from evolving cybersecurity threats. Partnering with a reliable infrastructure provider, such as Serverwala Data Center, can strengthen pipeline security by offering secure, scalable, and resilient hosting solutions tailored to meet modern CI/CD requirements.
We at Serverwala provide high-performance dedicated servers with robust security measures, perfect for supporting secure CI/CD operations. Their services include multiple layers of physical and network security, which help protect against unauthorized access and ensure continuous monitoring. With a 99.99% uptime SLA and 24/7 technical support, Serverwala enables businesses to maintain high availability and real-time responsiveness in their CI/CD processes, minimizing interruptions that could otherwise lead to vulnerabilities.
Additionally, the data center market is experiencing a massive expansion, expected to reach $517 billion by 2030, driven largely by digital transformations and the adoption of automated CI/CD pipelines. By leveraging Serverwala’s secure hosting environment, companies can scale confidently, knowing that their data and deployment processes are well-protected against security risks.